Cutting-Edge BQT Biometrics Australia for Improved Security and Safety
Cutting-Edge BQT Biometrics Australia for Improved Security and Safety
Blog Article
Maximizing Business Protection: The Ultimate Overview to Electronic Security Solutions
In the fast-paced and ever-evolving landscape of organization protection, the reliance on digital protection options has actually come to be vital for protecting important properties, private info, and preserving functional connection. In this overview to digital safety and security services, we will certainly check out the most current fads, cutting-edge innovations, and finest practices to strengthen your business against possible dangers and susceptabilities.
Significance of Electronic Security Solutions
When taking into consideration the protection of possessions and sensitive details, the importance of digital safety and security solutions can not be overemphasized. In today's interconnected globe, where cyber hazards are continuously developing and coming to be a lot more advanced, companies must prioritize implementing robust electronic protection steps to protect their data and procedures. Digital security remedies encompass a vast array of innovations and methods developed to prevent unauthorized gain access to, data breaches, malware, and other cyber threats.
Among the crucial advantages of electronic safety and security services is their capacity to provide real-time tracking and danger detection. BQT Locks. Via devices like intrusion detection systems, firewalls, and safety details and event monitoring (SIEM) systems, organizations can proactively recognize and reply to protection incidents prior to they rise into significant violations. In addition, electronic safety solutions assist make sure conformity with industry guidelines and criteria, safeguarding services from potential lawful and financial repercussions
Sorts Of Electronic Protection Solutions
Given the essential significance of digital safety and security services in guarding organizations against cyber threats, it is vital to discover the different types of digital protection systems readily available to boost security and durability. One of the most typical kinds of digital protection systems is the firewall program, which acts as an obstacle in between a business's interior network and external networks, filtering system out potentially hazardous data. By using a mix of these electronic safety systems, organizations can establish a robust defense versus various safety and security hazards.
Carrying Out Access Control Steps
Furthermore, gain access to control procedures can be integrated with surveillance systems to monitor and tape-record individuals' activities within safeguarded areas. This integration improves security by supplying a comprehensive review of who is accessing particular locations at any type of given time. Access control systems can be configured to limit accessibility based on time, place, or individual qualifications, allowing organizations to customize safety and security procedures according to their details demands.
Cybersecurity Finest Practices
To enhance total safety pose, executing durable cybersecurity finest practices is critical in safeguarding electronic possessions and data honesty. One fundamental technique is guaranteeing regular software application updates throughout all tools and systems to patch vulnerabilities promptly. Utilizing strong, one-of-a-kind passwords and carrying out multi-factor verification includes layers of protection against unapproved accessibility. Carrying out routine safety and security audits and analyses aids determine weaknesses and locations for enhancement. Employee training on cybersecurity recognition is crucial in protecting against social engineering attacks and making certain a security-conscious workforce.
Establishing a detailed incident action try this site strategy allows swift and efficient actions to safety violations, reducing potential damages. Securing delicate data both en route and at remainder offers an additional barrier versus data violations. Executing access controls based on the principle of the very least privilege limits the direct exposure of crucial systems and info to you could look here just those that require it for their functions. Routine back-ups of information ensure that in the event of a ransomware assault or information loss, critical information can be recuperated. Welcoming an aggressive approach to cybersecurity through constant tracking and hazard knowledge assists find and mitigate potential risks before they escalate. By integrating these finest methods right into cybersecurity approaches, organizations can strengthen their defenses versus evolving cyber threats.
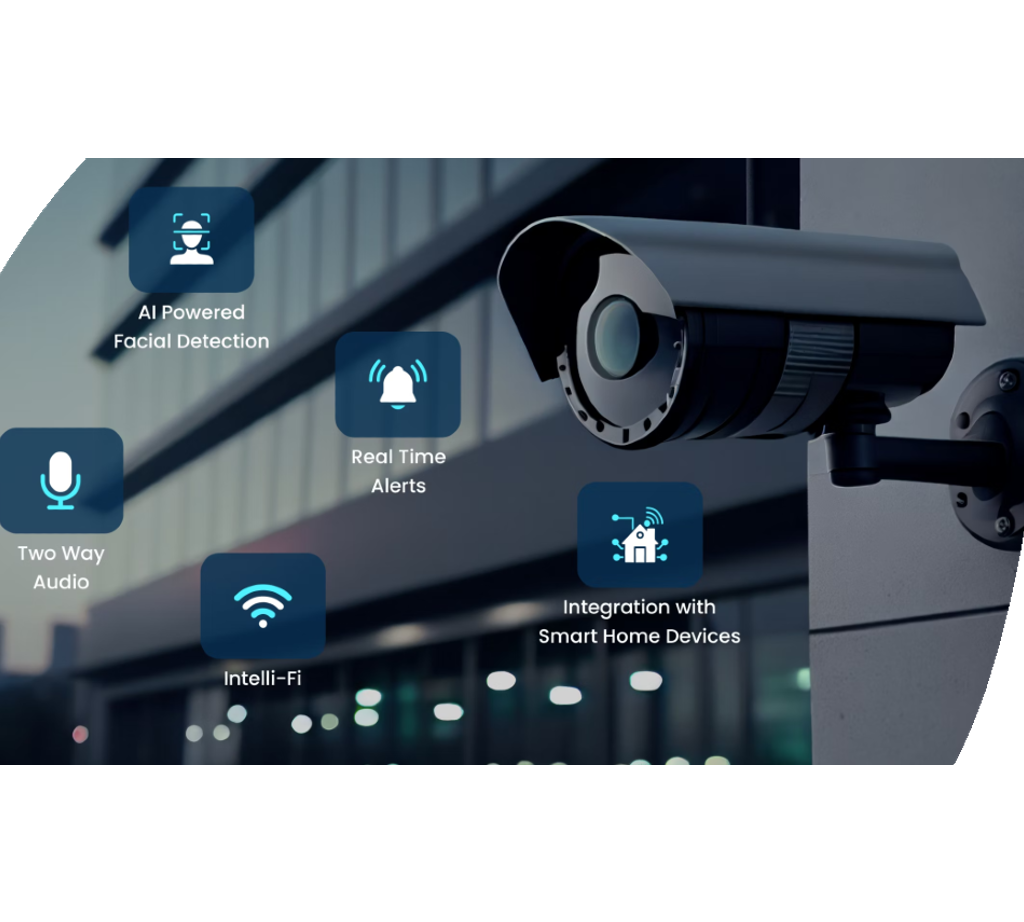
Surveillance and Surveillance Solutions

Video visit our website clip surveillance options offer remote tracking capacities, allowing licensed employees to keep an eye on the facilities also when off-site. Additionally, progressed attributes like motion detection, face acknowledgment, and license plate recognition boost the total safety and security pose of the company. Integrating monitoring systems with security system and accessibility control further enhances the safety infrastructure, enabling a proactive reaction to prospective safety violations.
Verdict
In conclusion, electronic protection remedies are necessary for making best use of service security. It is essential to invest in the appropriate electronic security systems to make certain the safety and security and safety of the organization.
Report this page